GitHub just-in-time (JIT) self-hosted Runners on AWS Fargate
The ECS Fargate task includes the container definition for our JIT runner, along with the URI of the associated ECR image.
A walkthrough for creating a sample task is covered in subsequent sections.
Task Definition for JIT Runner
Navigate to: “Amazon Elastic Container Service” > “Task definitions” > “Create new task definition“, and start entering details for the new task.
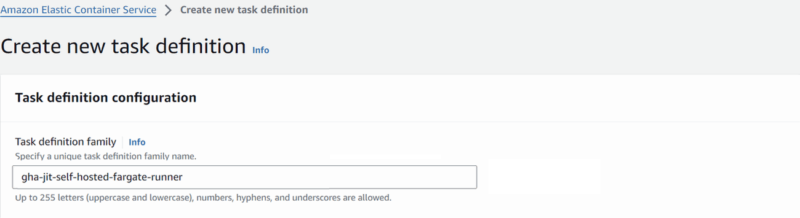
Task definition configuration
- Task definition family: gha-jit-self-hosted-fargate-runner
Infrastructure requirements
- Launch type: AWS Fargate
- OS, Architecture: Linux/x86_64
- Task role: ecsTaskIAM-Role
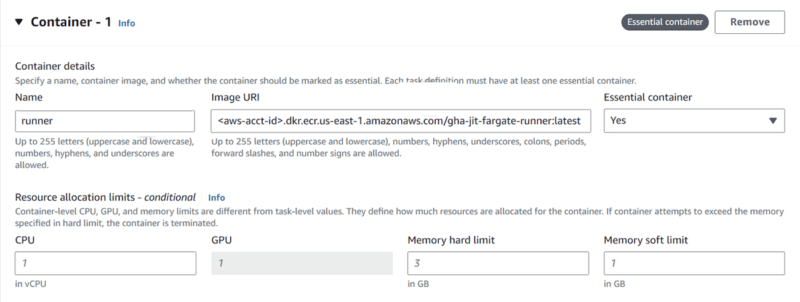
- Task size:
- CPU: 1 vCPU
- Memory: 3 GB
- Task execution role: ecsTaskExecutionRole

If the task and execution roles do not already exist, they will need to be created with the appropriate permission policies attached. Sample role/policy definitions used in this example are shown below.
Task Role: ecsTaskIAM-Role
| Policy name | ecsTaskIAMPolicy |
| Policy definition | { “Version”: “2012-10-17”, “Statement”: [ { “Sid”: “SQSAccess”, “Effect”: “Allow”, “Action”: [ “sqs:DeleteMessage”, “sqs:GetQueueUrl”, “sqs:ReceiveMessage”, “sqs:GetQueueAttributes” ], “Resource”: [ “arn:aws:sqs:<region>:<aws-acct-id>:git-actions-wf-job-queue” ] } ] } |
| Role trusted entities | { “Version”: “2012-10-17”, “Statement”: [ { “Sid”: “”, “Effect”: “Allow”, “Principal”: { “Service”: “ecs-tasks.amazonaws.com” }, “Action”: “sts:AssumeRole” } ] } |
Task Execution Role: ecsTaskExecutionRole
| Policy name | ecsTaskExecutionPolicy |
| Policy definition | { “Version”: “2012-10-17”, “Statement”: [ { “Sid”: “SQSAccess”, “Effect”: “Allow”, “Action”: [ “sqs:DeleteMessage”, “sqs:GetQueueUrl”, “sqs:ReceiveMessage”, “sqs:GetQueueAttributes” ], “Resource”: [ “arn:aws:sqs:<region>:<aws-acct-id>:git-actions-wf-job-queue” { “Version”: “2012-10-17”, “Statement”: [ { “Effect”: “Allow”, “Action”: [ “ecr:GetAuthorizationToken”, “ecr:BatchCheckLayerAvailability”, “ecr:GetDownloadUrlForLayer”, “ecr:BatchGetImage”, “logs:CreateLogStream”, “logs:PutLogEvents” ], “Resource”: “*” }, { “Effect”: “Allow”, “Action”: [ “secretsmanager:GetSecretValue” ], “Resource”: [ “arn:aws:secretsmanager:<region>:<aws-acct-id>:secret:github-actions-runner-registration-token-??????” ] } ] } |
| Role trusted entities | { “Version”: “2012-10-17”, “Statement”: [ { “Sid”: “”, “Effect”: “Allow”, “Principal”: { “Service”: “ecs-tasks.amazonaws.com” }, “Action”: “sts:AssumeRole” } ] } |
Container – 1
Container details
- Name: runner
- Image URI: <aws-acct-id>.dkr.ecr.<region>.amazonaws.com/gha-jit-fargate-runner:latest
Environment variables
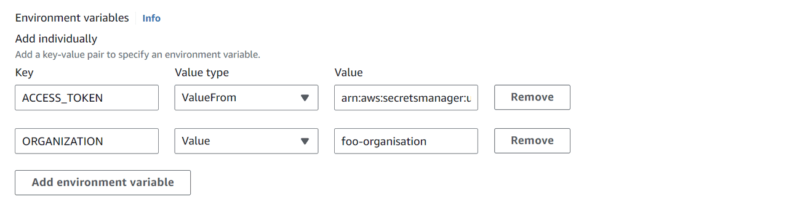
| Variable name | Description | Sample Value |
|---|---|---|
| ORGANIZATION | The GitHub organization name that the JIT self-hosted runner will register to. In this example, the organization name foo-organisation has been used. http://github.com/foo-organisation | foo-organisation |
| ACCESS_TOKEN | AWS secretsmanager ARN which holds the Personal Access token (PAT) for the associated GitHub organization. The token is used to generate a JIT runner configuration for the target GitHub organization. In this example, the token was generated for GitHub organization: foo-organisation. | arn:aws:secretsmanager:<region>:<aws-acct-id>:secret:github-actions-runner-registration-token |
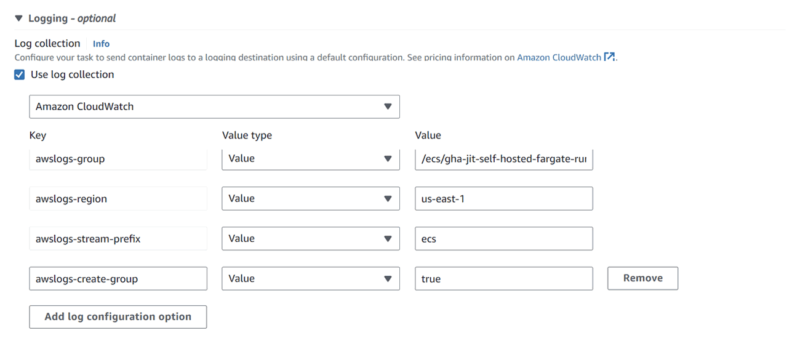
Logging
Log collection
- Use log collection: ticked
- Logging destination: Amazon CloudWatch
- awslogs-group: /ecs/gha-jit-self-hosted-fargate-runner
- awslogs-region: target AWS region
- awslogs-stream-prefix: ecs
- awslogs-create-group: true
- Other settings for the task can remain set with default values.